Hack Prevention
How to Scan Your Server for Exploits & Viruses: 5 Tools
Nothing can be more frustrating than working so hard for months to build a quality online portal only to see it hacked and defaced. If you are not paying attention to what you are uploading to your server, that is exactly what’s going to happen. We have already covered WordPress plugins you can use to protect your website and make it harder to hack. These 5 exploit scanners are worth exploring too:
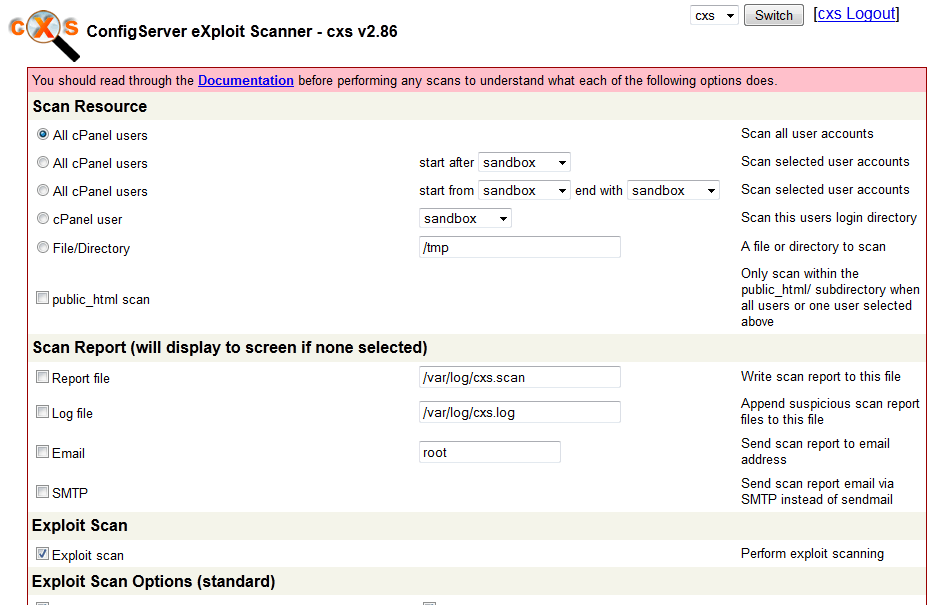
ConfigServer eXploit Scanner: a premium solution that allows you to take a more proactive approach to server security. It scans your files for exploit script fingerprint matches, identifies suspicious files, and mitigates symlink attacks. It uses ClamAV to scan for viruses.
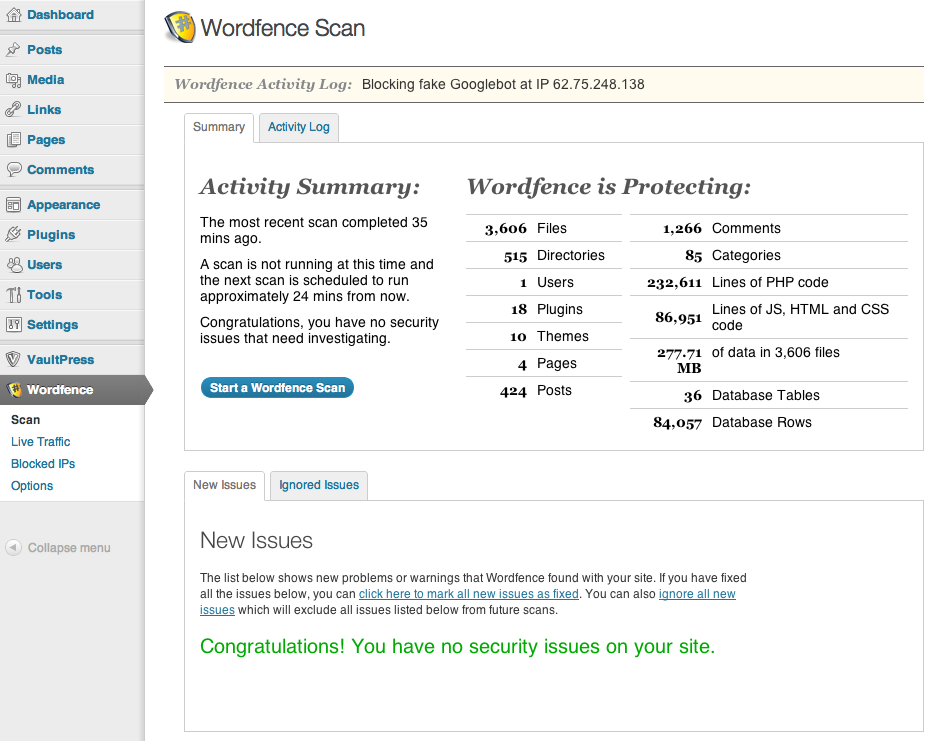
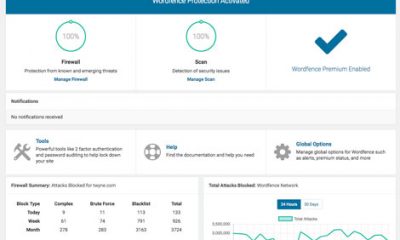
WordFence: a free security plugin that adds a firewall, virus scanning, and real-time traffic tracking to your website. It can help you repair your files just in case you don’t have backups.
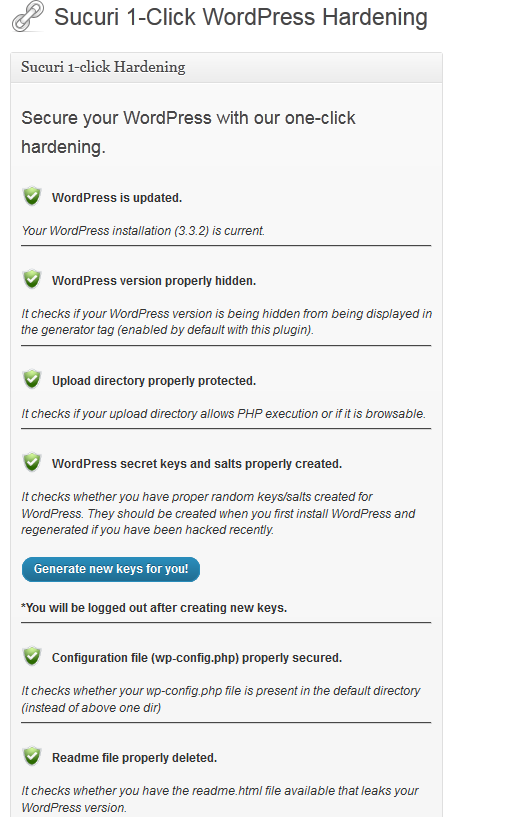
Sucuri: should not need any introduction. These guys are behind some great WordPress security tools. They can help you identify and fix potential issues with your website. Their server side tools could prove very useful too.
Anti-Gumblar: a free script that checks your uploaded files and quarantines files that are suspicious. It can kill live FTP connections of attackers.
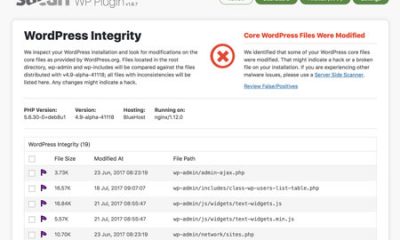
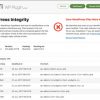
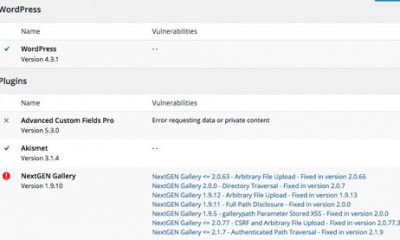
Exploit Scanner: a WordPress plugin that scans the files on your website, your posts, and comments to find suspicious items. It can potentially save you from using malicious plugins.
You won’t need all these solutions to keep your server secure. We have had a lot of success with CXS and Sucuri in the past. You should test a few of these to see which one works the best for your environment. Don’t forget to take time to harden WordPress for maximum protection.