Hack Prevention
How to Fix Hacked WordPress Sites: Step by Step
Getting hacked is one of the worst experiences one can go through as a webmaster. Unfortunately, no matter how careful you are, there is always a chance that a smart hacker might get around your defenses. That does not mean you should just give up and do not do your best to protect your website against future hack attacks. Fixing a hacked website is not always difficult. In fact, it can be a very time consuming process.
Troubleshooting & Fixing Hacked WordPress Sites
In order to fix your website and get it back to its original condition, you first have to analyze what has happened. Sometimes all hackers do is deface sites and manipulate their .htaccess files. Those are not that hard to fix. Database and server hacks are a bit more consuming to get a handle on though.
Determine the method of hack
Fixing your website is important. But you also need to understand how you were hacked so you can avoid having to deal with the same issue in the future. There are commands you can run on your server to figure out how it was accessed and by whom.
![]()
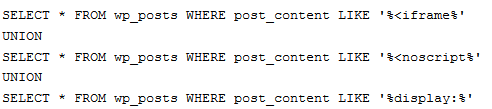
If you are with a decent web host, chances are its team has a guide on how to deal with hacked sites. You do want to pay attention to the date the files on your sites were changed. That helps you identify which files you need to take care of first (I would delete everything though). If your database has been altered, you are better off using a clean backup to save yourself some time in the process. Of course, you can always go through your database and use commands such as this to find malicious content in it:
Scan all your files
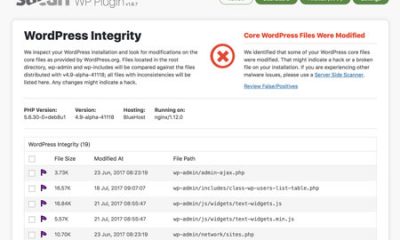
This is the first thing I would do after bringing all my sites down. The reason is quite simple. You do not want your website to be visited and flagged as having malware while you are in the process of fixing it. I always put my site in maintenance mode and go to work to fix some of the issues with it. You can use SSH to find the files that have been modified recently. But that is not always perfect and can be very time-consuming if you have multiple sites. I prefer downloading all the files from my server to my local machine and use a software such as BitDefender to look for viruses and other malicious codes.
This is not always the fastest method. If you do not want your website to be down for too long, you are better off removing your files and installing fresh ones while you scan your old files (I still would do the scanning to figure out which files were installed on my server). Do yourself a favor and use a clean computer to connect to your database and server.
Removed hacked files
The easiest way to make sure your site will be clean and without any backdoors. You should remove everything. That means everything except your WP-config file. Make sure you backup your theme files so you know how to re-do the custom changes you have made to it in the past. .htaccess files should also be removed and replaced with clean ones just to be on the safe side.
Remove unused themes and plugin
Going back to the previous point, you should remove everything that you do not need or use from your server. I can’t tell you how many times my sites have been hacked through unused themes. Many web hosts bundle their WordPress installer with bunch of exclusive free themes. I would delete all those too.
Install new scripts and themes right from their source
Always try to get the latest version of everything you intend to re-install on your website. Grab the plugins from WordPress.org (if possible). Make sure you use a secure FTP program to transfer the new files to the server. Those of you who are using a premium theme should contact your developer to get the latest copy of your template.
Refresh your database
Finding hacks in your database is not always easy. If you have been making backups of your database, you can restore it quickly and get on your way. Things will be a bit more tricky if you have not saved backups of your database or don’t know which version you have is actually clean.
Change all passwords
If you have found yourself with a hacked account, you should change your WordPress, FTP, email and database passwords. Don’t just stop there. When my sites on DreamHost were hacked, I changed everything that looked like a password. I am of course kidding here. But do yourself a favor and choose a super strong password for your accounts.
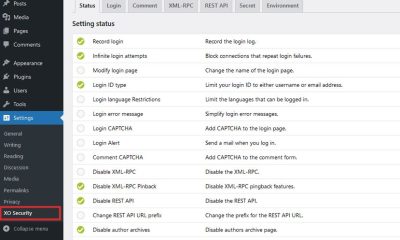
Harden WordPress
My lazy side made me skip this step in the past. But I learned my lesson the hard way. Hardening WordPress is not terribly difficult but can take a bit of time.
- Update WordPress: you should always take time to update your WordPress install as fast as possible. Not tomorrow but today! I have seen some webmasters that are still using super old WordPress code for no specific reason. That is not a very smart move.
- Watch permissions on your site: make sure your files and directories have the right permissions. WordPress.org already has a ton of useful information on this.
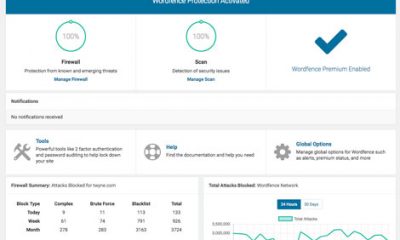
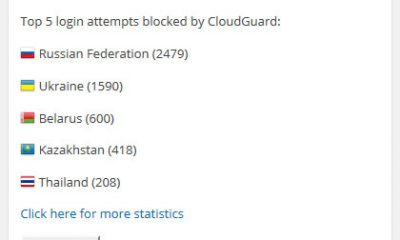
- Address web server vulnerabilities: you should always try to partner with a decent web host. If your hosting partner keeps getting hacked, it is probably time for you to move. There are security solutions such as CloudFlare and DotDefender that could stop some of those hack attacks. Always consult with your web host’s support team to find ways you can secure your server.
- Use strong passwords: goes without saying. Your passwords should not be easy to guess. Also they should not be just letter or numbers.
- Use secure FTP: using regular FTP to connect to your site is very risky. You never know who may be listening. SFTP gives you a better chance to stay protected while transferring files to your account.
- Secure wp-admin & wp-include: these may be a bit more challenging for WordPress users who are not that technical. But WordPress already has some great information to get you started here. Don’t forget to block access to scripts and directories that should not be accessible to other users.
- Protect your wp-config file: you should move the wp-config.php file to the directory above your WordPress install. The file should be readable only to you.
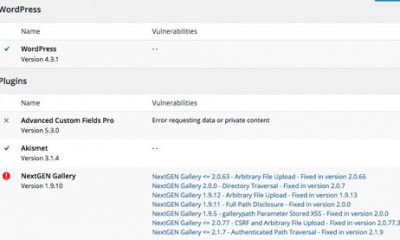
- Use security plugins: we have covered plenty of firewall and anti-malware plugins here in the past. These plugins do not identify and stop all hacks but they do provide another layer of security.
- Change admin, table prefix, security keys: all WordPress webmasters should change their default “admin” username as soon as possible. You can easily do so through phpMyAdmin. The same applies to your table prefix (see security through obscurity). Finally, don’t forget to change your security keys in your wp-config file after fixing your hacked website.
- Hide things: the less information you leave out in the open, the better off your site will be. Hackers should not have an easy time figuring out which plugins and scripts you are running on your website. Also, if you happen to have multiple blogs on your server, make sure you keep their databases under separate usernames. Your visitors should not be able browse your directories either.
Backup WordPress
You should be already doing this. But it is always wise to check your backup process to make sure it actually works. I have had a lot of success using BackupBuddy. We have already covered plenty of plugins you can use to send your backup files to Dropbox and other cloud-storage services.
Monitor & secure your server
I don’t know about you but I don’t have time to monitor my server and sites for changes every day. The good news is there are plenty of services you can use to do the job for you. I use Sucuri for my own sites. CodeGuard is another powerful website monitoring service. It lets you backup your site and rollback changes that have been made to it.
What’s next?
Fixing a hacked WordPress site can be quite time consuming. Your goal should not only be to fix your site but also to avoid future hack attacks from succeeding. By following the above steps and hardening WordPress and your server software, you will stand a better chance to make that happen.